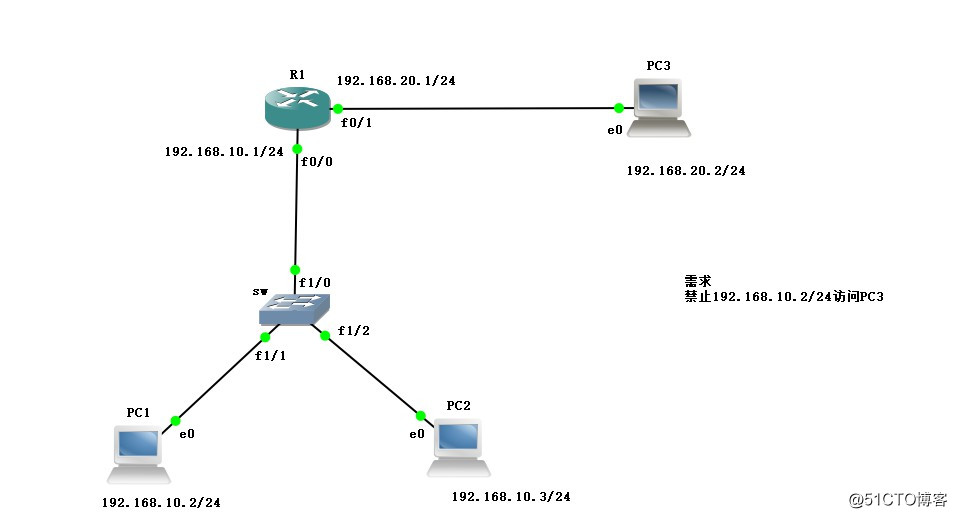
标准访问控制列表在GNS 3中拓扑实验,配置一台路由设备,一台交换设备,分别连接三台PC机,三台PC机分别配置IP地址,并在路由设备中配置网关,如下图所示,配置完成后配置标准访问控制列表,禁止PC1与
.
标准访问控制列表
在GNS 3中拓扑实验,配置一台路由设备,一台交换设备,分别连接三台PC机,三台PC机分别配置IP地址,并在路由设备中配置网关,如下图所示,配置完成后配置标准访问控制列表,禁止PC1与PC3通信,PC2与PC3正常通信。
1、首先进入交换设备进行配置
sw#conf t //进入全局模式Enter configuration commands, one per line. End with CNTL/Z.sw(config)#no ip routing //进入交换设备,关闭路由功能sw(config)#int f1/0 //进入f1/0接口sw(config-if)#speed 100 //配置速率100sw(config-if)#duplex full //开启双工模式2、进入路由设备,配置接口IP地址
R1#conf t //进入全局模式Enter configuration commands, one per line. End with CNTL/Z.R1(config)#int f0/0 //进入f0/0接口R1(config-if)#ip add 192.168.10.1 255.255.255.0 //添加IP地址R1(config-if)#no shutdown //开启接口R1(config-if)#int f0/1 //进入f0/1接口R1(config-if)#ip add 192.168.20.1 255.255.255.0 //添加IP地址R1(config-if)#no shutdown //开启接口R1(config-if)#exitR1(config)#do show ip routeCodes: C - connected, S - static, R - RIP, M - mobile, B - BGP D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2 E1 - OSPF external type 1, E2 - OSPF external type 2 i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2 ia - IS-IS inter area, * - candidate default, U - per-user static route o - ODR, P - periodic downloaded static routeGateway of last resort is not setC 192.168.10.0/24 is directly connected, FastEthernet0/0C 192.168.20.0/24 is directly connected, FastEthernet0/13、分别进入PC机,设置IP地址
PC1> ip 192.168.10.2 192.168.10.1Checking for duplicate address...PC1 : 192.168.10.2 255.255.255.0 gateway 192.168.10.1PC2> ip 192.168.10.3 192.168.10.1Checking for duplicate address...PC1 : 192.168.10.3 255.255.255.0 gateway 192.168.10.1PC3> ip 192.168.20.2 192.168.20.1Checking for duplicate address...PC1 : 192.168.20.2 255.255.255.0 gateway 192.168.20.14、先测试PC1与PC2是否可以与PC3通信
PC1> ping 192.168.20.2192.168.20.2 icmp_seq=1 timeout84 bytes from 192.168.20.2 icmp_seq=2 ttl=63 time=20.913 ms84 bytes from 192.168.20.2 icmp_seq=3 ttl=63 time=14.960 ms84 bytes from 192.168.20.2 icmp_seq=4 ttl=63 time=17.917 msPC2> ping 192.168.20.284 bytes from 192.168.20.2 icmp_seq=1 ttl=63 time=19.021 ms84 bytes from 192.168.20.2 icmp_seq=2 ttl=63 time=23.997 ms84 bytes from 192.168.20.2 icmp_seq=3 ttl=63 time=21.941 ms84 bytes from 192.168.20.2 icmp_seq=4 ttl=63 time=13.966 ms5、在路由设备中配置标准访问控制列表,禁止PC1与PC3通信
R1(config)#access-list 1 deny 192.168.10.2 0.0.0.0 R1(config)#do show access-listStandard IP access list 1 10 deny 192.168.10.2R1(config)#access-list 1 permit any R1(config)#do show access-listStandard IP access list 1 10 deny 192.168.10.2 20 permit anyR1(config-if)#ip access-group 1 in6、测试PC1是否可以与PC3通信
PC1> ping 192.168.20.2*192.168.10.1 icmp_seq=1 ttl=255 time=9.943 ms (ICMP type:3, code:13, Communication administratively prohibited)*192.168.10.1 icmp_seq=2 ttl=255 time=3.990 ms (ICMP type:3, code:13, Communication administratively prohibited)*192.168.10.1 icmp_seq=3 ttl=255 time=9.014 ms (ICMP type:3, code:13, Communication administratively prohibited)7、测试PC2与PC3是否可以正常通信
PC2> ping 192.168.20.2192.168.20.2 icmp_seq=1 timeout192.168.20.2 icmp_seq=2 timeout84 bytes from 192.168.20.2 icmp_seq=3 ttl=63 time=17.958 ms84 bytes from 192.168.20.2 icmp_seq=4 ttl=63 time=19.981 ms扩展访问控制列表
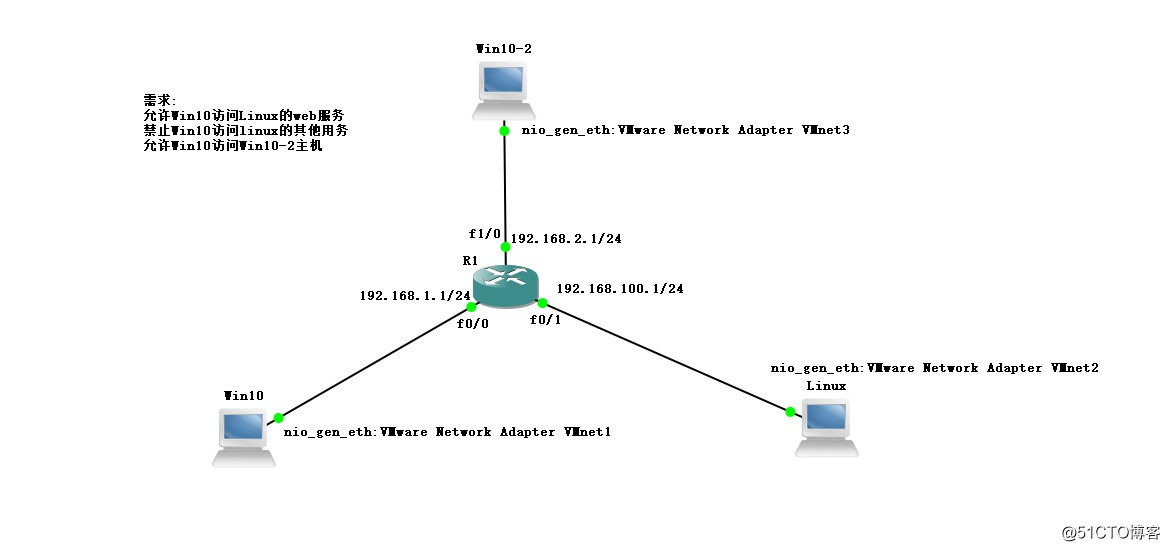
实验需求:
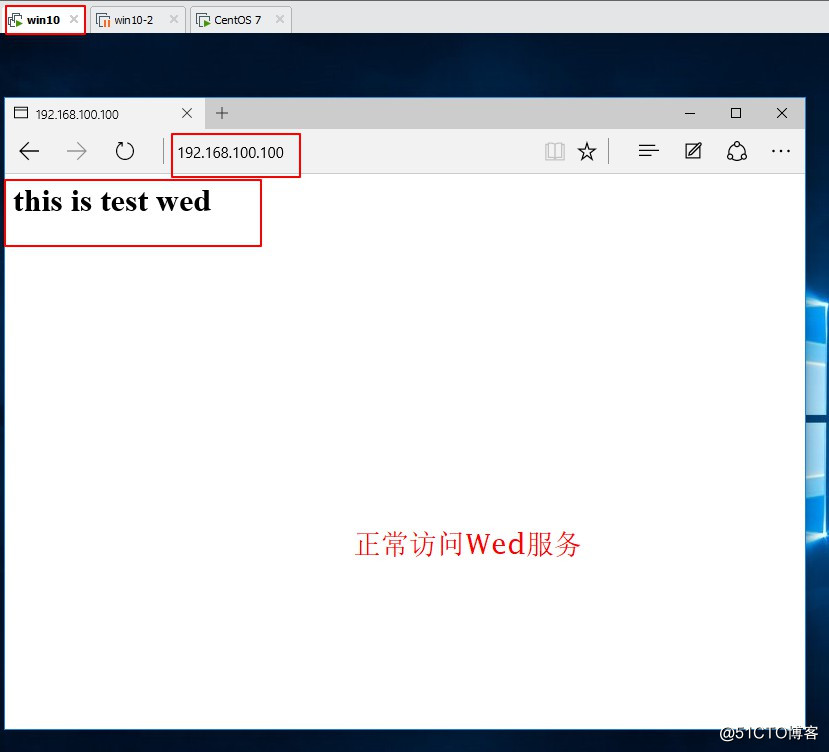
允许Win10访问Linux的web服务
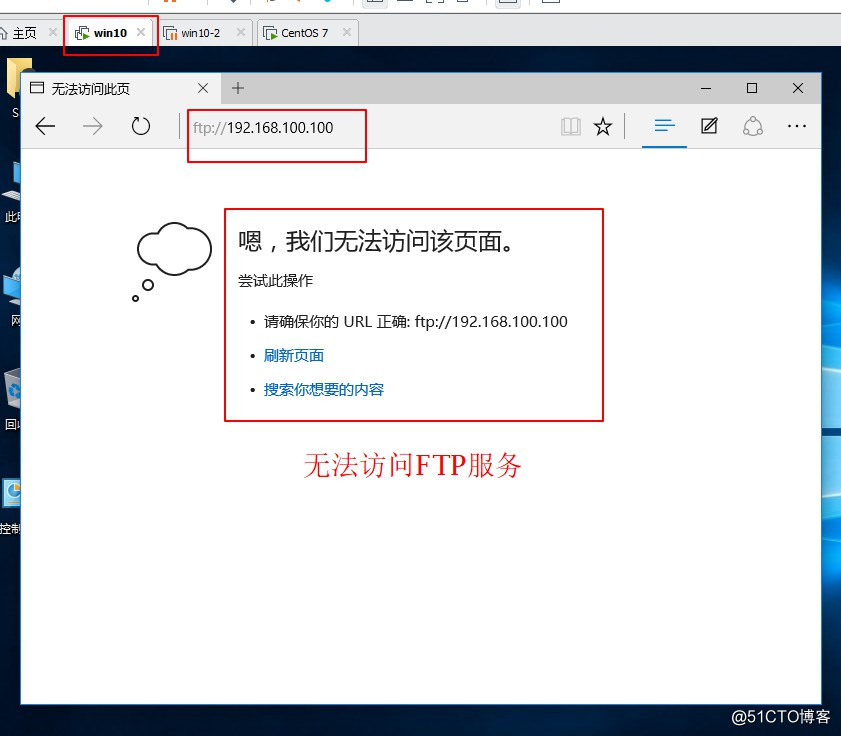
禁止Win10访问linux的其他用务
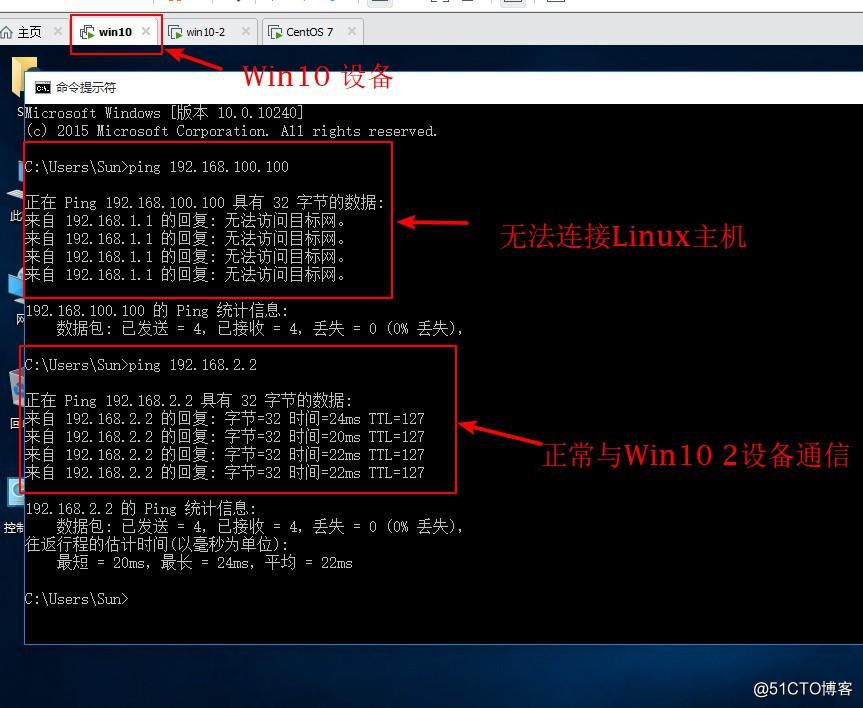
允许Win10访问Win10-2主机
首先在GNS 3中拓扑实验图,配置一台路由设备,在路由设备中添加一个网络接口,配置三台真实主机,一台Linux系统,两台win10系统,分别连接路由设备,并在VMware中开启主机,给三台主机分别绑定VMnet1、VMnet2、VMnet3网卡,然后分别与路由器相连,并在路由器接口处标出将要划分的三个网段,如图:
 1、在Linux系统中安装FTP与HTTP服务
1、在Linux系统中安装FTP与HTTP服务
[root@localhost ~]# yum install vsftpd -y已加载插件:fastestmirror, langpacksbase | 3.6 kB 00:00:00 extras | 2.9 kB 00:00:00 updates | 2.9 kB 00:00:00 (1/4): base/7/x86_64/group_gz | 165 kB 00:00:00 ...//省略部分内容...Running transaction 正在安装 : vsftpd-3.0.2-25.el7.x86_64 1/1 验证中 : vsftpd-3.0.2-25.el7.x86_64 1/1 已安装: vsftpd.x86_64 0:3.0.2-25.el7 完毕![root@localhost ~]# yum install httpd -y已加载插件:fastestmirror, langpacksLoading mirror speeds from cached hostfile * base: mirrors.nju.edu.cn...//省略部分内容...已安装: httpd.x86_64 0:2.4.6-90.el7.centos 作为依赖被安装: apr.x86_64 0:1.4.8-5.el7 apr-util.x86_64 0:1.5.2-6.el7 httpd-tools.x86_64 0:2.4.6-90.el7.centos mailcap.noarch 0:2.1.41-2.el7 完毕!2、更改Linux系统中网卡信息,并在VMware中绑定VMnet2网卡并重启虚拟机。
[root@localhost ~]# vim /etc/sysconfig/network-scripts/ifcfg-ens33TYPE=EthernetPROXY_METHOD=noneBROWSER_ONLY=noBOOTPROTO=staticDEFROUTE=yesIPV4_FAILURE_FATAL=noIPV6INIT=yesIPV6_AUTOCONF=yesIPV6_DEFROUTE=yesIPV6_FAILURE_FATAL=noIPV6_ADDR_GEN_MODE=stable-privacyNAME=ens33UUID=2ef6b862-5201-48c5-a450-23b3720ab3a0DEVICE=ens33ONBOOT=yesIPADDR=192.168.100.100NTEMASK=255.255.255.0GATEWAY=192.168.100.1~~:wq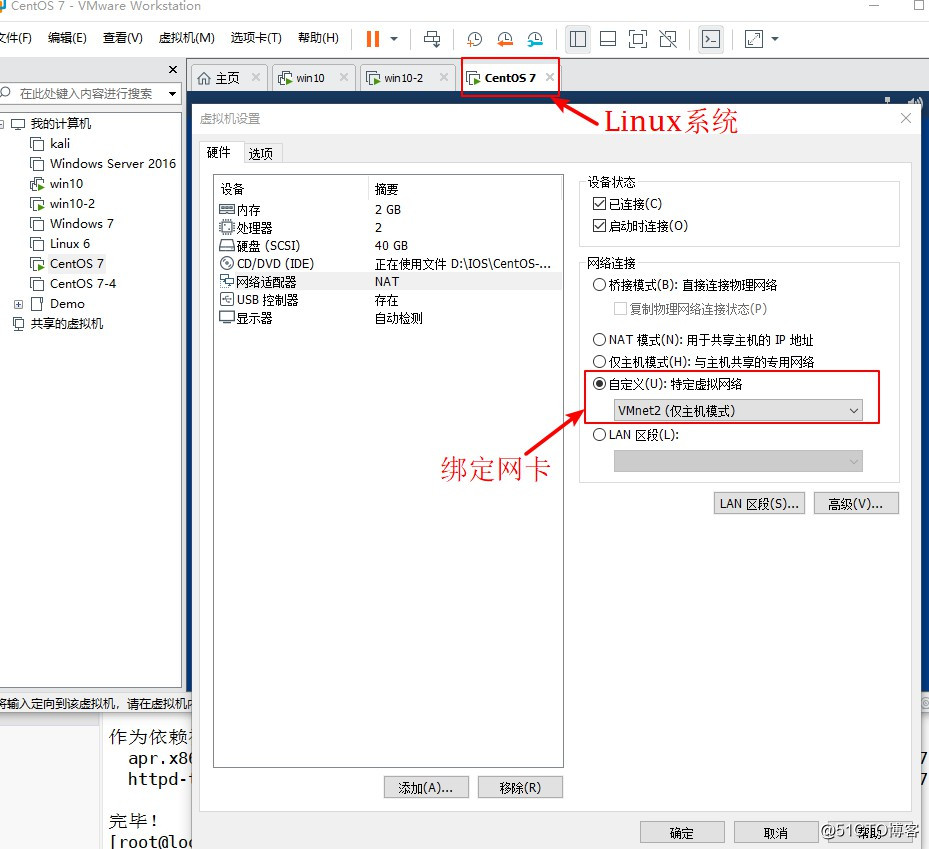
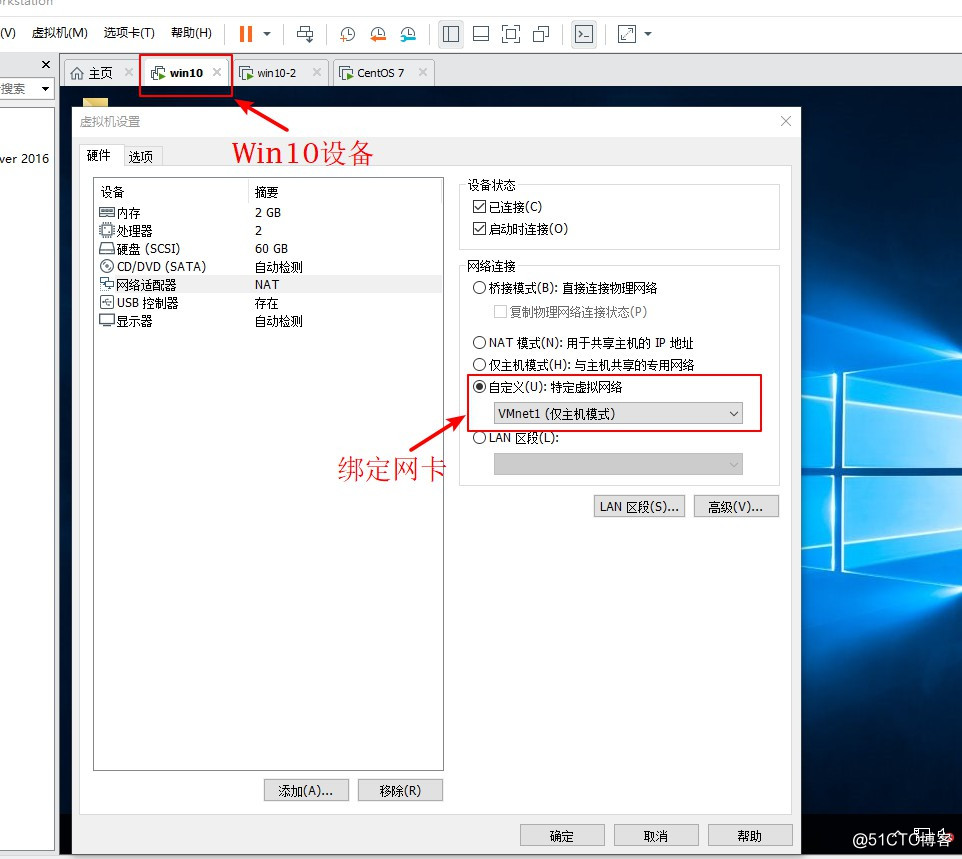
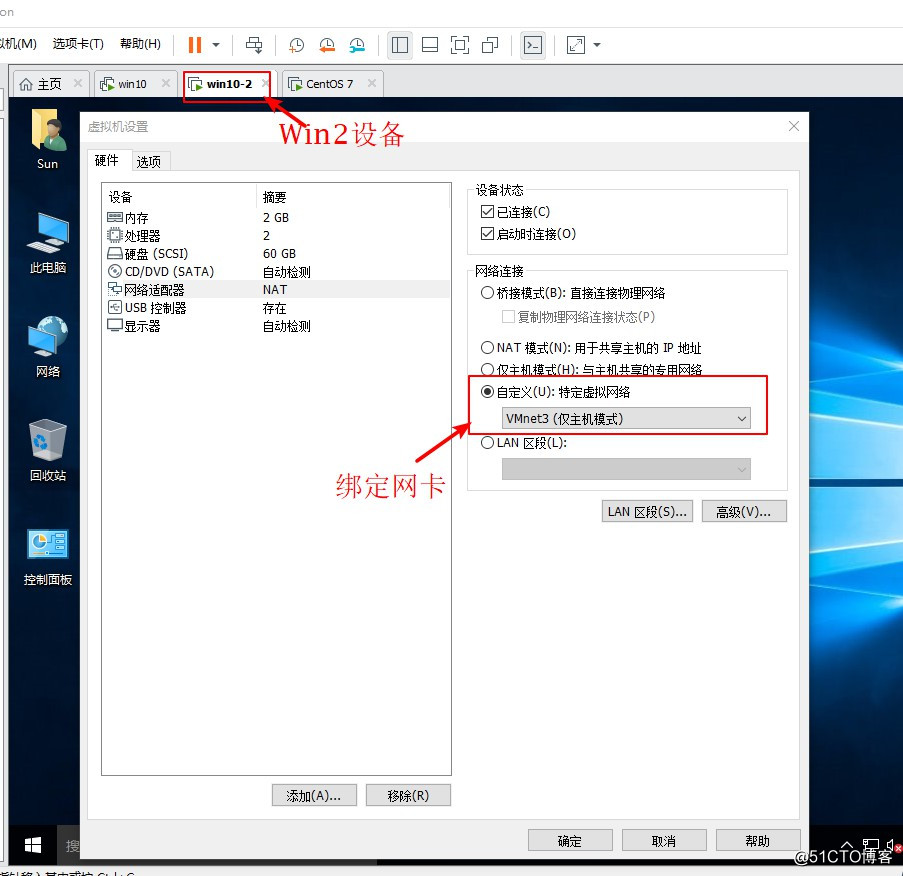
3、分别给两台Win10设备绑定网,然后分别配置固定IP地址,并关闭防火墙。
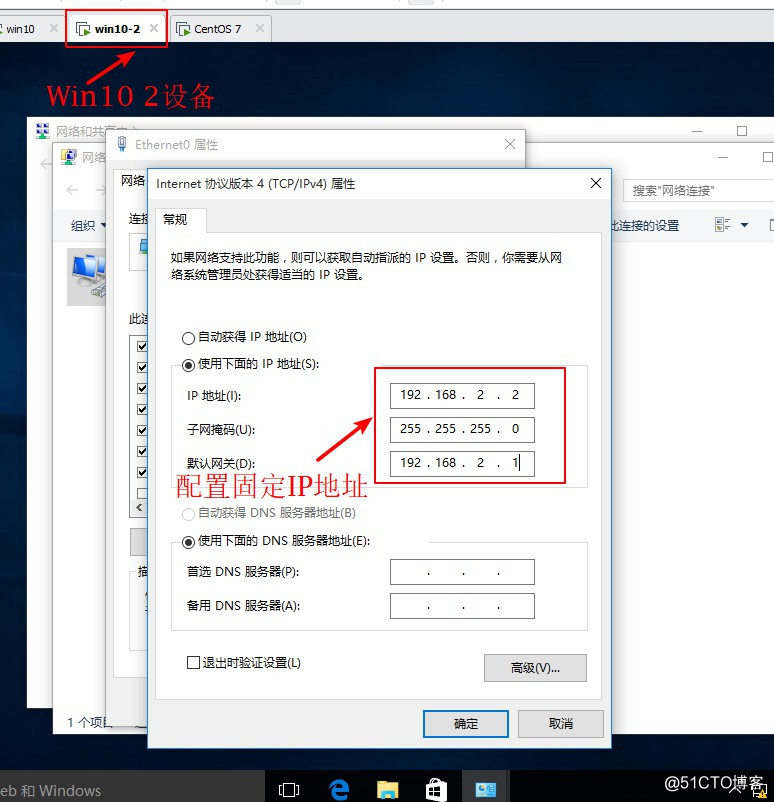
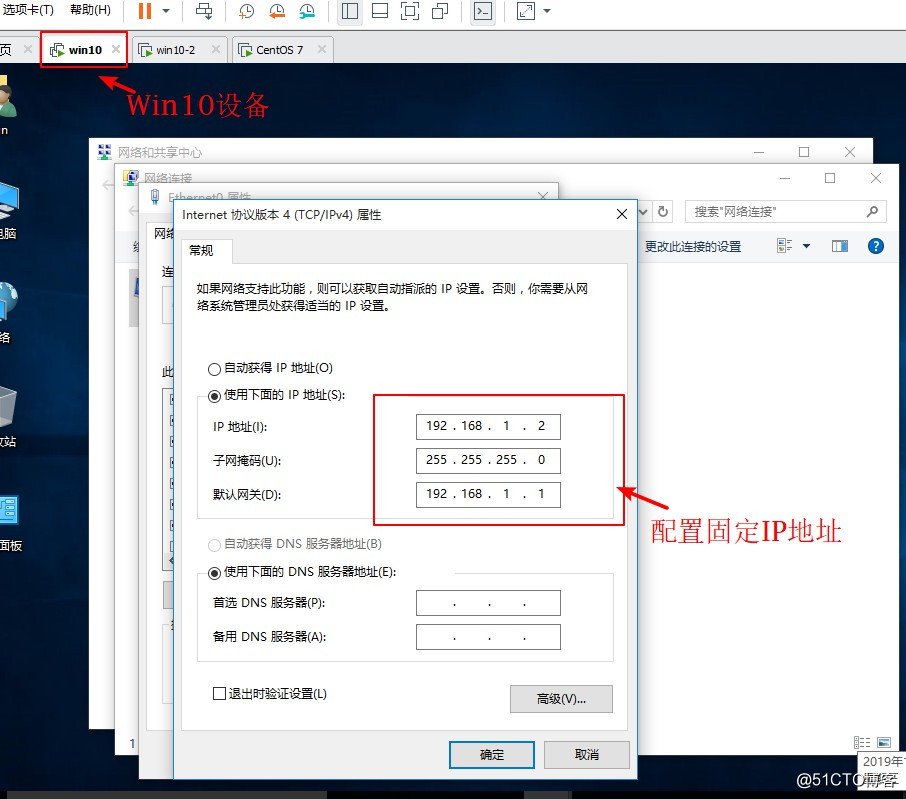
4、在GNS 3中开启设备,并进路由入设备进行配置接口IP地址
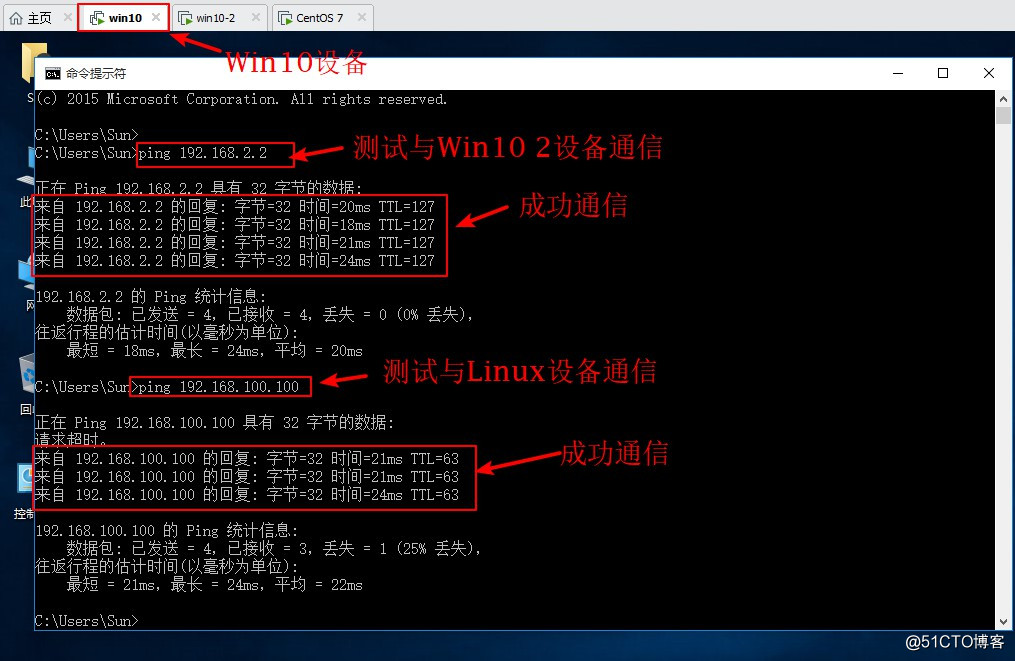
R1#conf t //进入全局模式Enter configuration commands, one per line. End with CNTL/Z.R1(config)#int f0/0 //进入f0/0接口R1(config-if)#ip add 192.168.1.1 255.255.255.0 //配置IP地址R1(config-if)#no shut //开启接口*Mar 1 00:05:30.323: %LINK-3-UPDOWN: Interface FastEthernet0/0, changed state to up*Mar 1 00:05:31.323: %LINEPROTO-5-UPDOWN: Line protocol on Interface FastEthernet0/0, changed state to upR1(config-if)#int f0/1 //进入f0/1接口R1(config-if)#ip add 192.168.100.1 255.255.255.0 //配置IP地址R1(config-if)#no shut //开启接口*Mar 1 00:06:16.031: %LINK-3-UPDOWN: Interface FastEthernet0/1, changed state to up*Mar 1 00:06:17.031: %LINEPROTO-5-UPDOWN: Line protocol on Interface FastEthernet0/1, changed state to upR1(config-if)#int f1/0 //进入f1/0接口R1(config-if)#ip add 192.168.2.1 255.255.255.0 //配置IP地址R1(config-if)#no shut //开启接口*Mar 1 00:06:35.815: %LINK-3-UPDOWN: Interface FastEthernet1/0, changed state to up*Mar 1 00:06:36.815: %LINEPROTO-5-UPDOWN: Line protocol on Interface FastEthernet1/0, changed state to upR1(config-if)#do show ip route //查看路由表Codes: C - connected, S - static, R - RIP, M - mobile, B - BGP D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2 E1 - OSPF external type 1, E2 - OSPF external type 2 i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2 ia - IS-IS inter area, * - candidate default, U - per-user static route o - ODR, P - periodic downloaded static routeGateway of last resort is not setC 192.168.1.0/24 is directly connected, FastEthernet0/0C 192.168.2.0/24 is directly connected, FastEthernet1/0 //显示网段信息C 192.168.100.0/24 is directly connected, FastEthernet0/15、测试网络连通性
6、在Linux系统中编辑HTTP服务站点信息,并启动服务,启动FTP服务。
[root@localhost ~]# cd /var/www/html/ //进入站点[root@localhost html]# vim index.html //编辑网页<h1>this is test wed</h1> //编辑内容~~:wq //保存退出[root@localhost html]# systemctl start httpd //启动httpd服务[root@localhost html]# systemctl stop firewalld.service //关闭防火情[root@localhost html]# setenforce 0 //关闭增强性安全功能[root@localhost html]# systemctl start vsftpd //启动FTP服务[root@localhost html]# netstat -ntap | egrep '(21|80)' //查看服务是否端口tcp6 0 0 :::80 :::* LISTEN 3437/httpd tcp6 0 0 :::21 :::* LISTEN 3766/vsftpd [root@localhost html]# cd /var/ftp/ //进入FTP站点[root@localhost ftp]# echo "this is ftp" > ftp_test.txt //生成txt文件[root@localhost ftp]# ls //查看站点内容ftp_test.txt pub //显示站点内容7、在win10设备中测试HTTP与FTP服务是否提供。
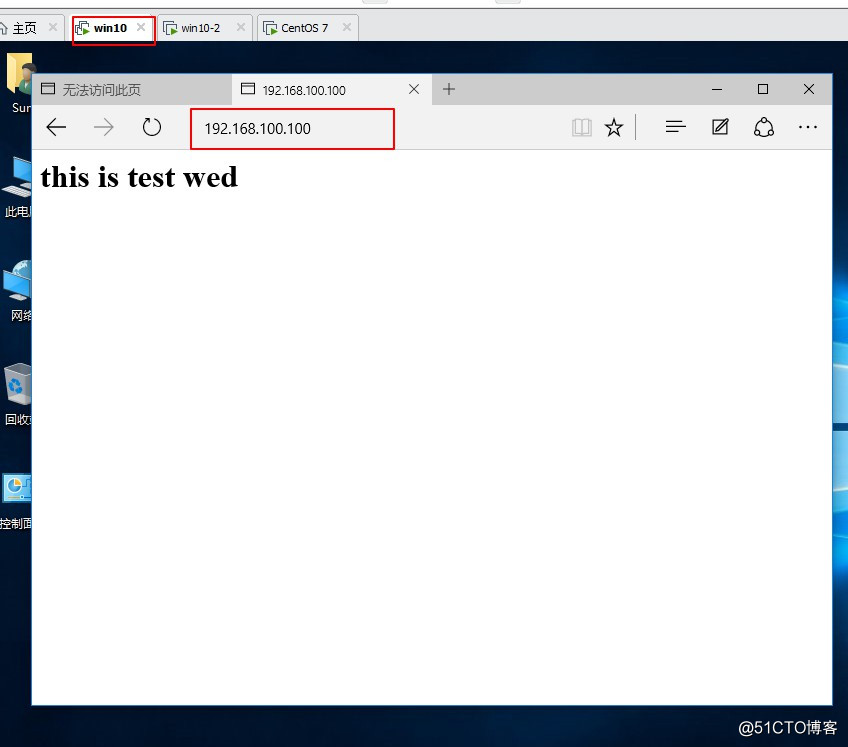
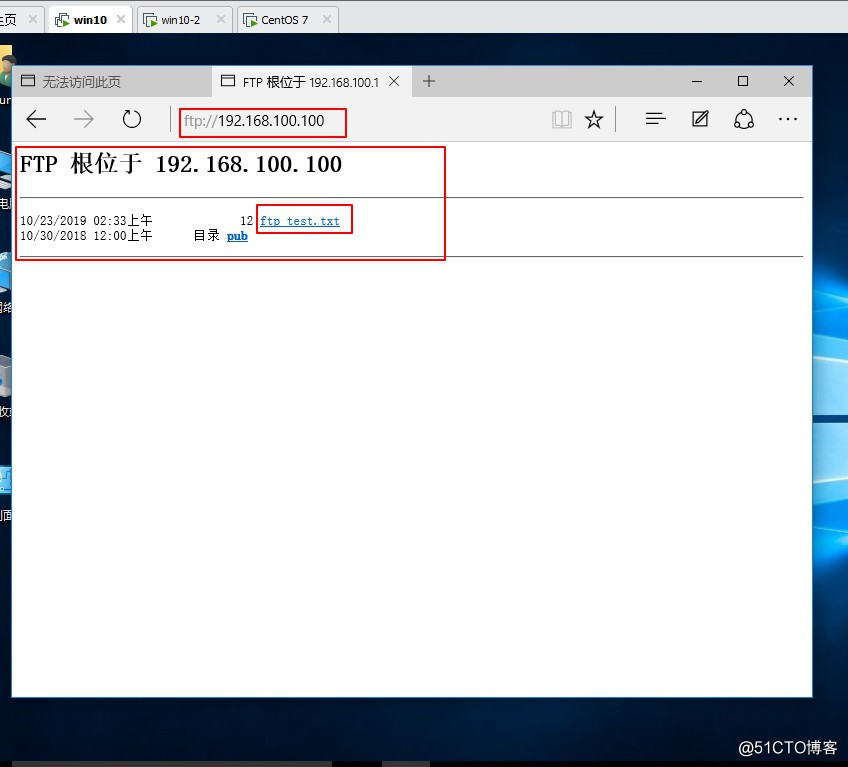
8、在GNS 3路由设备中配置ACL访问控制条目
R1(config)#access-list 100 per //设置win10主机允许访问Linux系统HTTP服务 R1(config)#$ 100 permit tcp host 192.168.1.2 host 192.168.100.100 eq wwwR1(config)#do show access-li //查看Extended IP access list 100 10 permit tcp host 192.168.1.2 host 192.168.100.100 eq www //显示列表信息R1(config)#access-list 100 deny ip host 192.168.1.2 host 192.168.100.100 //配置拒绝访问Linux其他服务R1(config)#do show access-li //查看 Extended IP access list 100 10 permit tcp host 192.168.1.2 host 192.168.100.100 eq www 20 deny ip host 192.168.1.2 host 192.168.100.100 //显示列表信息R1(config)#access-list 100 permit ip host 192.168.1.2 192.168.2.0 0.0.0.255 //配置win10设备允许访问win10 2设备R1(config)#do show access-li //查看 Extended IP access list 100 10 permit tcp host 192.168.1.2 host 192.168.100.100 eq www 20 deny ip host 192.168.1.2 host 192.168.100.100 30 permit ip host 192.168.1.2 192.168.2.0 0.0.0.255 //显示列表信息R1(config)#int f0/0 //进入接口R1(config-if)#ip access-group 100 in //将配置应用在接口,进入方向9、测试配置结果