实验拓扑图:实验目的:武汉分公司和哈尔滨总部通过ipsec v p n 建立连接,实现两边内网互相访问。主要记录ipsec的配置。预先配置好模拟环境,武汉和哈尔滨的pc可以正常去访问公网,也就是这个区
.
实验拓扑图:
实验目的:
武汉分公司和哈尔滨总部通过ipsec v p n 建立连接,实现两边内网互相访问。
主要记录ipsec的配置。
预先配置好模拟环境,武汉和哈尔滨的pc可以正常去访问公网,也就是这个区域的网络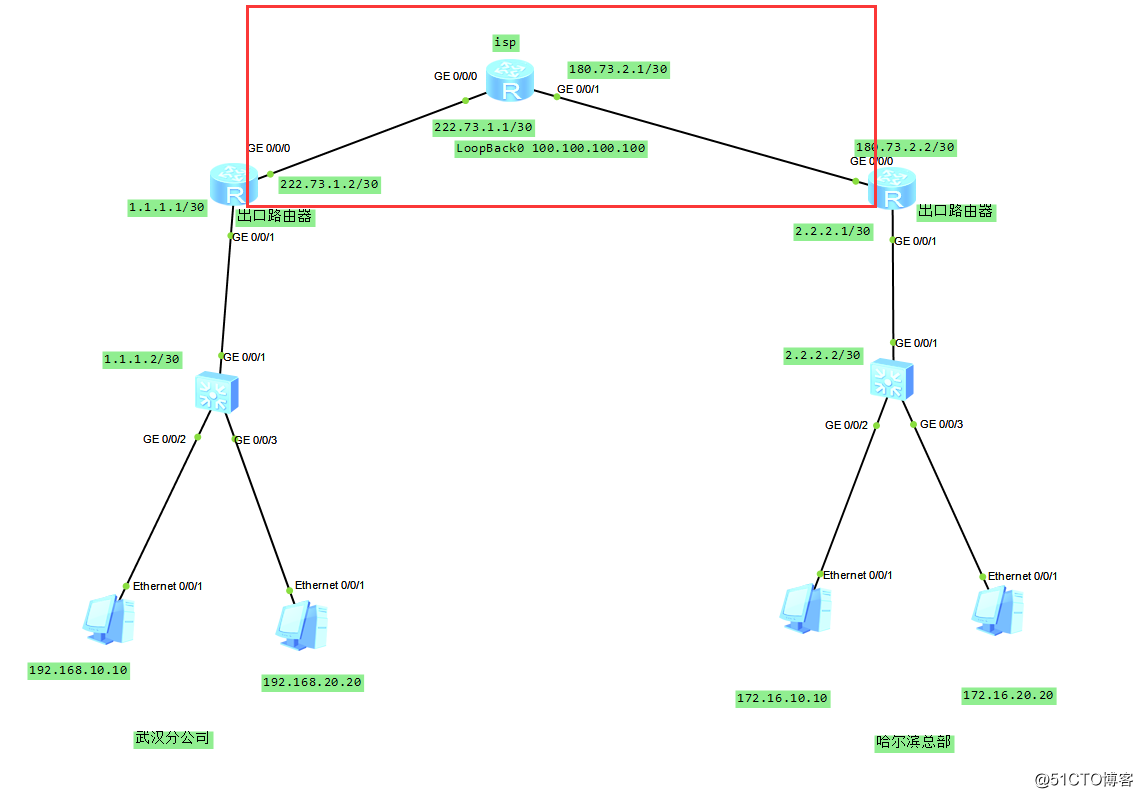
武汉出口路由配置:
<wuhan-r>dis ip rout | in StaRoute Flags: R - relay, D - download to fib------------------------------------------------------------------------------Routing Tables: Public Destinations : 12 Routes : 12 Destination/Mask Proto Pre Cost Flags NextHop Interface0.0.0.0/0 Static 60 0 RD 222.73.1.1 GigabitEthernet0/0/0192.168.0.0/16 Static 60 0 RD 1.1.1.2 GigabitEthernet0/0/1<wuhan-r>哈尔滨出口路由配置:
<wuhan-r>dis ip rout | in StaRoute Flags: R - relay, D - download to fib------------------------------------------------------------------------------Routing Tables: Public Destinations : 12 Routes : 12 Destination/Mask Proto Pre Cost Flags NextHop Interface0.0.0.0/0 Static 60 0 RD 222.73.1.1 GigabitEthernet0/0/0192.168.0.0/16 Static 60 0 RD 1.1.1.2 GigabitEthernet0/0/1<wuhan-r>武汉nat配置:
<wuhan-r>dis acl 2000Basic ACL 2000, 1 ruleAcl's step is 5rule 10 permit source 192.168.0.0 0.0.255.255 <wuhan-r>dis nat ou <wuhan-r>dis nat outbound NAT Outbound Information:-------------------------------------------------------------------------Interface Acl Address-group/IP/Interface Type-------------------------------------------------------------------------GigabitEthernet0/0/0 2000 222.73.1.2 easyip -------------------------------------------------------------------------Total : 1<wuhan-r>哈尔滨nat配置:
<haerb-r>dis acl 2000Basic ACL 2000, 1 ruleAcl's step is 5 rule 10 permit source 172.16.0.0 0.0.255.255 <haerb-r>dis nat out <haerb-r>dis nat outbound NAT Outbound Information: -------------------------------------------------------------------------- Interface Acl Address-group/IP/Interface Type -------------------------------------------------------------------------- GigabitEthernet0/0/0 2000 180.73.2.2 easyip -------------------------------------------------------------------------- Total : 1<haerb-r>二层配置不做介绍。
现在武汉和哈尔滨内部pc可以正常上网。但是武汉和哈尔滨pc不能相互访问,这个时候配置ipsec v pn实现武汉和哈尔滨能内网能相互访问。
“配置采用手工方式建立IPSec隧道”
1,分别在wuhan-r和haerb-r上配置ACL,定义各自要保护的数据流
武汉:
[wuhan-r]dis acl 3000Advanced ACL 3000, 2 rulesAcl's step is 5 rule 5 permit ip source 192.168.0.0 0.0.255.255 destination 172.16.0.0 0.0.255.255 rule 10 permit ip source 222.73.1.2 0.0.0.252 destination 172.16.0.0 0.0.255.255哈尔滨:
[haerb-r]dis acl 3000Advanced ACL 3000, 2 rulesAcl's step is 5 rule 5 permit ip source 172.16.0.0 0.0.255.255 destination 192.168.0.0 0.0.255.255 rule 10 permit ip source 180.73.2.2 0.0.0.252 destination 192.168.0.0 0.0.255.255注意:我这里各加了一条rule 10,原因是我要保护的数据流同时也是nat的ip段,所有这里把nat装换后的ip加进去。
2,分别在wuhan-r和haerb-r上创建IPSec安全提议
武汉:
[wuhan-r]display ipsec proposal name tran1IPSec proposal name: tran1 Encapsulation mode: Tunnel Transform : esp-new ESP protocol : Authentication SHA2-HMAC-256 Encryption AES-128哈尔滨:
[haerb-r]dis ipsec proposal name tran1IPSec proposal name: tran1 Encapsulation mode: Tunnel Transform : esp-new ESP protocol : Authentication SHA2-HMAC-256 Encryption AES-1283,分别在wuhan-r和haerb-r上创建安全策略
武汉:
[wuhan-r] ipsec policy whtohaerb 10 manual[wuhan-r-ipsec-policy-manual-map1-10] security acl 3000[wuhan-r-ipsec-policy-manual-map1-10] proposal tran1[wuhan-r-ipsec-policy-manual-map1-10] tunnel remote 180.73.2.2[wuhan-r-ipsec-policy-manual-map1-10] tunnel local 222.73.1.2[wuhan-r-ipsec-policy-manual-map1-10] sa spi outbound esp 12345[wuhan-r-ipsec-policy-manual-map1-10] sa spi inbound esp 54321[wuhan-r-ipsec-policy-manual-map1-10] sa string-key outbound esp cipher antiy[wuhan-r-ipsec-policy-manual-map1-10] sa string-key inbound esp cipher antiy[wuhan-r-ipsec-policy-manual-map1-10] quit哈尔滨:
[haerb-r] ipsec policy haerbtowh 10 manual[haerb-r-ipsec-policyl-manual-use1-10] security acl 3000[haerb-r-ipsec-policyl-manual-use1-10] proposal tran1[haerb-r-ipsec-policyl-manual-use1-10] tunnel remote 222.73.1.2[haerb-r-ipsec-policyl-manual-use1-10] tunnel local 180.73.2.2[haerb-r-ipsec-policyl-manual-use1-10] sa spi outbound esp 54321[haerb-r-ipsec-policyl-manual-use1-10] sa spi inbound esp 12345[haerb-r-ipsec-policyl-manual-use1-10] sa string-key outbound esp cipher antiy[haerb-r-ipsec-policyl-manual-use1-10] sa string-key inbound esp cipher antiy[haerb-r-ipsec-policyl-manual-use1-10] quit此时分别在wuhan-r和haerb-r上执行display ipsec policy会显示所配置的信息
[wuhan-r]dis ipsec policy name whtohaerb ===========================================IPSec policy group: "whtohaerb"Using interface: GigabitEthernet0/0/0=========================================== Sequence number: 10 Security data flow: 3000 Tunnel local address: 222.73.1.2 Tunnel remote address: 180.73.2.2 Qos pre-classify: Disable Proposal name:tran1 Inbound AH setting: AH SPI: AH string-key: AH authentication hex key: Inbound ESP setting: ESP SPI: 54321 (0xd431) ESP string-key: aUUOJ`$]T*KQ=^Q`MAF4<1!! ESP encryption hex key: ESP authentication hex key: Outbound AH setting: AH SPI: AH string-key: AH authentication hex key: Outbound ESP setting: ESP SPI: 12345 (0x3039) ESP string-key: aUUOJ`$]T*KQ=^Q`MAF4<1!! ESP encryption hex key: ESP authentication hex key:[haerb-r]display ipsec policy name haerbtowh ===========================================IPSec policy group: "haerbtowh"Using interface: GigabitEthernet0/0/0=========================================== Sequence number: 10 Security data flow: 3000 Tunnel local address: 180.73.2.2 Tunnel remote address: 222.73.1.2 Qos pre-classify: Disable Proposal name:tran1 Inbound AH setting: AH SPI: AH string-key: AH authentication hex key: Inbound ESP setting: ESP SPI: 12345 (0x3039) ESP string-key: aUUOJ`$]T*KQ=^Q`MAF4<1!! ESP encryption hex key: ESP authentication hex key: Outbound AH setting: AH SPI: AH string-key: AH authentication hex key: Outbound ESP setting: ESP SPI: 54321 (0xd431) ESP string-key: aUUOJ`$]T*KQ=^Q`MAF4<1!! ESP encryption hex key: ESP authentication hex key: 4,分别在wuhan-r和haerb-r的接口上引用各自的安全策略,使接口具有IPSec的保护功能
武汉:
[wuhan-r-GigabitEthernet0/0/0]dis th[V200R003C00]#interface GigabitEthernet0/0/0 ip address 222.73.1.2 255.255.255.252 ipsec policy whtohaerb nat outbound 2000#return哈尔滨:
[haerb-r-GigabitEthernet0/0/0]dis th[V200R003C00]#interface GigabitEthernet0/0/0 ip address 180.73.2.2 255.255.255.252 ipsec policy haerbtowh nat outbound 2000#return验证:
武汉公司内网192.168.10.10可以正常ping哈尔滨公司内网172.16.10.10
执行命令display ipsec statistics esp可以查看数据包的统计信息
[wuhan-r]display ipsec statistics esp Inpacket count : 16 Inpacket auth count : 0 Inpacket decap count : 0 Outpacket count : 14 Outpacket auth count : 0 Outpacket encap count : 0 Inpacket drop count : 0 Outpacket drop count : 0 BadAuthLen count : 0 AuthFail count : 0 InSAAclCheckFail count : 0 PktDuplicateDrop count : 0 PktSeqNoTooSmallDrop count: 0 PktInSAMissDrop count : 0“采用默认配置通过IKE协商方式建立IPSec隧道”
参考:https://support.huawei.com/enterprise/zh/routers/ar2200-pid-6078842?category=configuration-commissioning
.



